T Office © - Offensive Network Security.
T Office ©
Offensive Network Security
T Office © Cyber Warfare
- T Office © provides with my 37 years as EH in the shadows of clearweb and deep web incl. dark web expertise in the art of Offensive Network Security you can't as hacker buy. You must live and earned it.
- Many Network Security Companies claim to have the best hackers. That might be, all Cred to them, but the truth is educations as CEH among other pentest exams are good to have, but 37 years of hands-on experience of hacking is better.
The best is a combination of decades of hands-on experience of Offensive Network Security and education in computer science, programming and network security:
- A combination that T Office © provide.
- Many caught black- and grey hats are claimed by media to be best the hackers.
That might be, all Cred to them, but don't forget that it takes knowledge to stay under the radar on the scene, in three decades.
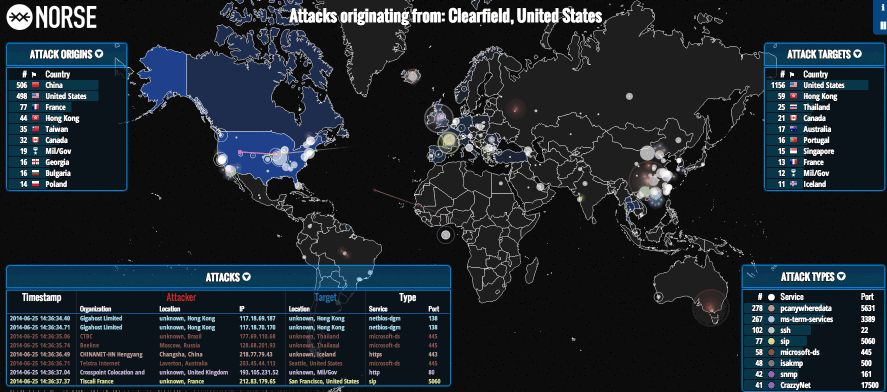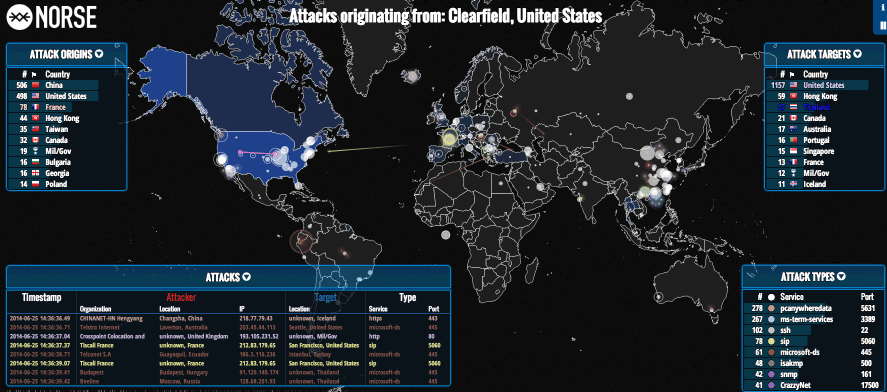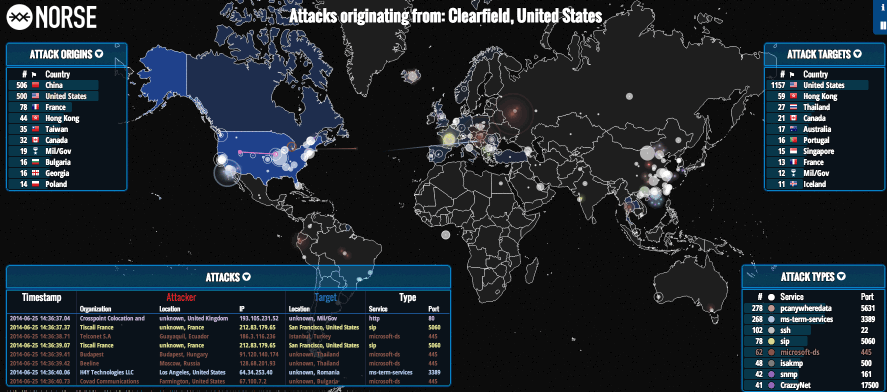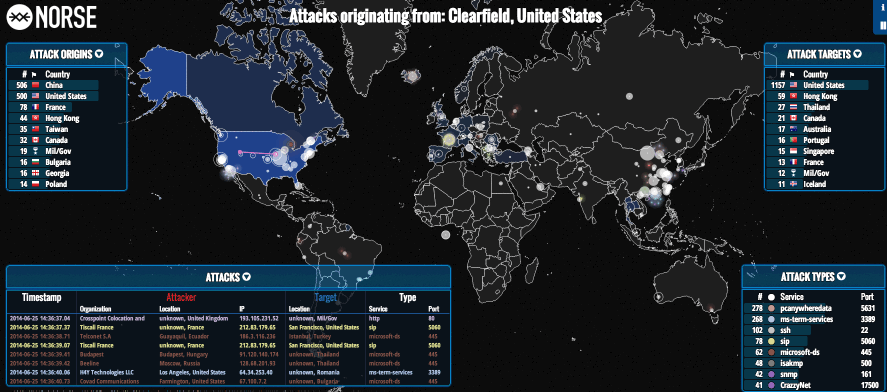
After 2016 the most of us understand that a "silent" cyber war is taking place. The targets are not only democratic elections, but also companies. This cyber warfare includes assaults on important infrastructure as we have seen in e g Sweden, attacks on the economy and on critical management in the society.
In addition to the security dangers involving infrastructure, the deep involvement of computer related technologies in our lives exposes us to dangers which didn't exist before.
For example in the medical field, electronic imaging, medical carts, computerized life-saving equipment, computerized hospital emergency rooms, and computerized operating rooms, are all at risk of cyber attacks. This have allready happened in Sweden.
But it don't stop there as T Office © can show with hacking vehicles, airport scanners, heathers in appartments, surveillance cameras, pacemakers, credit cards, access cards, passports, e-ID cards and even computer batteries. Computer batteries sounds harmless, but with right knowledge you can make some of them explode. And you can make pacemakers stop.
Due to the rich technological attack potential in the past few years, we are witnessing more complex attacks which are more specific and multi-faceted, due to the knowledge acquired in computerized attack methodology combined with knowledge in additional sectors such as chemical industry, finance sector, electricity industry, transportation sector and more.
Counter-act problems before problems become problems,
Petrus Toxy
/ Petrus Toxy
Founder of T Office © - Offensive Network Security
"I take pride in hunting down cyber threats.
I don't perform ICT Forensics and ICT Security as a 9-5 work
- my goal is to achieve success
- always in all ways."
/ Petrus Toxy
T Office © have, when performing services:
- Corporate insurance;
- Insurance against liability;
- Legal security;
- Property insurance.
T Office © support following projects:
- EFF (legal help);
- Tor Project (factotum);
- Transifex (translation).

T Office is a proud user of Lua.

