T Office © - Offensive Network Security.
T Office ©
Offensive Network Security
T Office © Cyber threats
"..bring the madness..". / Pegboard Nerd
"..bring the madness.." This is what the cyber world has become to. Far beyond what the original pioneers of Internet in the late 60's and 70's could have forseen. / Petrus Toxy
Updated 12 / 01 2017
Advanced persistent threats (APTs)
A targeted cyber espionage or cyber sabotage attack that is usually sponsored by a nation state with the goal of stealing information from an organization. The motivation behind an advanced persistent threat is to gain information for military, political, or economic advantage.
Some of the largest ATP sponsoring countries are: China, Iran, Russia, UK, USA.
Adware
A program that generates popups on your computer or displays advertisements.
The software will automaticlly plays, displays, or downloads advertisements to a computer, often in exchange for the right to use a program without paying for it.
The advertisements seen are based on monitoring of browser habits. Most adware is safe to use, but some can serve as spyware, gathering information about you from your hard drive, the websites you visit, or even your keystrokes. Certain types of adware have the capability to capture or transmit personal information and can be used by companies as T Office ©.
Adware exists to advertise some commercial entity actively and without the user's permission or awareness, for example by replacing banner ads on web pages with those of another content provider.
Note. There are many legitimate programs that are given for free which display ads in their programs in order to generate revenue. As long as this information is provided up front then they are generally not considered malware.

Anonymous
Then I don't see Anonymous (Anon) as whole, as a threat to western democracy and the Free world, I will not go deeper into Anon as a cyber threath. As a Legal counselor I believe in individual responsibility and not in collective punishment. I also believe in western democracy and freedom of speech.
Yet I can say, as I understand everyone can be Anon. The only one need is a computer and Internet. With that said, there is not one Anon. Inside Anon there are many Anons.
A group of Anons can be one Anon or a legion of Anons. Every individual or group can have their own AnonOps, #op or sometimes share interests. Or not. Some seem to be driven by being tricksters, some others by political causes. Some are just bystanders seeking lulz. Nowhere in Anons ideal is stipulated that Anon must stand together or even like other Anons. In fact claiming own entities, fractal chaos and diversity is right in the line with the original hackers from MIT in '50s, '60s, '70s and the modern day start of Internet anno 1993/1994. Just accept the differences or move on to your own IRC.
No one is in the position to say what Anon are or not are. One part of the scene seem to be take the easy sharp pen and play the game by the playing field rules. It seem to mean not to be an individual public medial show-off or play the game with an unsharp broad pen, a pen that leak inc everywhere.
Anon seem to be a colective nom de plume, Janus faces and sometimes Connoisseurs of forbidden fruit.
Note. Petrus Toxy Law Firm offers via EFF pro bono legal help to hacktivists.
T Office © do not work against the values of original hackers from MIT.
The only time T Office © help hunt hacktavists down, is if these individuals are working on the behalf of undemocratic groups such as terrorist organizations or countries that sponsors terrorism.
ATM skimming
A type of fraud or theft that occurs when an ATM (Bankomat in Swedish) is compromised with a skimming device. A card reader that can be disguised to look like a part of the machine. The card reader collects victims' account information and a spy camera collects the personal identification numbers (PIN).
It has since several years been possible hack ATM's. Russia is the country in the whole world were this is most common. USA is on thesecond place.
The newest threath is hacking the banksystem. In this way you can select e g 10 ATM's to spit out money. At the ATM the black hat have handyman's waiting. This has spread from Russia to eastern Europe.
Back-door
A trojan that allows a remote user to execute commands and tasks on your computer without your permission. These types of programs are typically used to launch attacks on other computers, distribute copyrighted software or media, or hack other computers through your computer. It is an urban myth that your computer can not be used by cyber criminals, if you use a router with password. Unfortunately we have cases where computer owners have been convicted, only on the base that their computer was used in cyber crime. It would be the same as you was convicted after someone took your car without asking and used it in a crime activity.
Computer programmers often build back-doors into software applications so they can fix bugs. If hackers learn about a back-door, the feature may pose a security risk. Then a hacker can through a back-door bypasse logins and passwords. Malware are often design to exploit back-doors (see Malware).
Back-door can also be referred to as a trap-door. Hackers can built back-doors after entering a system through an exploit (see below), a weak spot in the attack surface and after locking the flawn from inside.
The idea with locking from inside is to keep other hackers out, who also may have heard or found out of the exploit in the same attack surface.
Back-doors are used to communicate, give orders to the hacked system or/and drain the system out of information (passwords, logs, business secrets, geo positions, the targets habits etc.) and/or use the hacked system to attack new systems. The new attack can be random or remoted by geo position to specific targets.
Hackers can use OS natural ports for communication as exploits, for example ports used to netmeeting. These ports can be open without you using netmeeting. Also ports for e.g. DNS can be used. The idea can be redirect your computer. A hacker can also use weak spots in softwear by sending in e g a trojan. The trojan trick the system with its dropload and install its payload with different orders for e g "install yourself as an exe file, put the AV off, shut all updates off, create a back door, contact Master for new instructions" (but written in e g Python).
Hacker can protect the back-door from other hackers with differnt methods. One method used is cryptography. The last thing a hacker want is that an other hacker make a hostile takeover. E g a black hat can make good money through a hostile takeover of e g a whole network of hacked computers, i e zombies.
See Bot, Botnet, DDoS and Zombies below.
Banker
Banker is a trojan (see Trojan). Banker programs are designed to steal your account data for online banking systems, e-payment systems, and credit or debit cards.
Black hat hackers
Hackers who gain unauthorized access into a computer system or network with malicious intent. They may use computers to attack systems for profit, for fun, for political motivations, or as part of a social cause. Such penetration often involves modification and/or destruction of data, as well as distribution of computer viruses, Internet worms, and delivery of spam through the use of botnets.
Blended threat
A general description for malicious programs that combine elements of multiple types of malware: viruses, worms, Trojans etc. For example Stuxnet. Pure art.
Bluejacking Sending unsolicited messages over Bluetooth to Bluetooth-enabled devices such as mobile phones, PDAs, and laptop computers.
Bluesnarfing Unauthorized access to information such as a calendar, contact list, e-mails, and text messages on a wireless device through a Bluetooth connection.
BS Code
Code created of malware creators to bs with malware reverse engineers. A virtual yarn unravel. A lulz.
Bot
Short for "robot," a computer that has been infected with malicious software without the user's knowledge. Once the computer has been affected, a cyber criminal can send commands to it and other infected machines over the Internet. The computer is under control of a third part.
Since the compromised computers blindly follow the commands of the cyber criminals, infected machines are also called zombies (see below).
Botnet (bot network)
A botnet or robot network is a group of computers running a computer application controlled and manipulated only by the owner or the software source. The botnet may refer to a legitimate network of several computers that share program processing amongst them.
Usually though, when people talk about botnets, they are talking about a group of computers infected with the malicious kind of robot software, the bots, which present a security threat to the computer owner. Once the robot software (also known as malicious software or malware) has been successfully installed in a computer, this computer becomes a zombie or a drone, unable to resist the commands of the bot commander.
A botnet may be small or large depending on the complexity and sophistication of the bots used. A large botnet may be composed of ten thousand individual zombies. A small botnet, on the other hand may be composed of only a thousand drones. Usually, the owners of the zombie computers don't know that their computers and their computers’ resources are being remotely controlled and exploited by an individual or a group of malware runners through e g an Internet Relay Chat (IRC)
There are various types of malicious bots that have already infected and are continuing to infect the internet. Some bots have their own spreaders – the script that lets them infect other computers (this is the reason why some people dub botnets as computer viruses) – while some smaller types of bots do not have such capabilities.
A botnet can consist of a network of 10.000 - 100.000 computers a k a bots. But. For example Storm had 200.000+ active bots in a 24 h period. The largest botnet has been thirty (30) million computers large.
Not all botnet are built up of hijacked computers. Some botnet are voluntary. Most botnet are not.
The computer becomes often a member of a unvolontary botnet by getting infected by malware. This is the traditional way. Methods are many. The malware can be in a fun video you watch, malicious link you hit, an e-mail from your mother you open, a piggyback on a software you load.
Today you also become infected through drive-by downloads so prevalent that you are getting infected without realizing it.
Often a hacker want to infect computers with best possible brandwidth such as corporate, government and University computers.
The malware can be blended. For example the Storm are a worm, rootkit, spam relay, and trojan all in one. But it can also be a simple worm as Rbot.
A botnet can works in many ways. One way is connecting it to an IRC server and channel. Large botnet as Storm do not use IRC. Then the master behind the botnet would need a server on anabolics to manage it. The master behind Storm would probably not even want to connect via IRC. Instead botnet as Storm use peer-to-peer a k a P2P. It is safer for the Master. P2P is as a HTTP botnet harder to detect. The weakness for complex botnet as Storm is same time their strength - encryption. It is safer for the Master, but it leaves patterns. In the same way as for example TOR does in countries as e.g. Sweden. Patterns stand out in fuzzy information / data. Patterns you can rewind and track down. But a IRC server can serve for example botnet as Rbot (i.e. malware).
Once the connection is made to an IRC server and a hidden channel a k a Command and Control channel a k a C&C, the computers waits for their Master a k a herder, often the same person who infected the computers in the first place. Usually the herder is waiting in C&C and looking as more and more infected computers a k a zombies (see Zombie) join.
The herder can goes before an attack back and forth between deep-/ dark web chat channels and in the dark web hidden C&C channel to orchestre the attack. Zombies hover on C&C until their herder gives them a order, for example "ddos 194.318.15.1 (fictitious IP)" (see DDoS). Sudden all zombies start attack the given IP address. (see IP address), till the IP address goes down. There are ways to prevent DDoS in the same way as for example spamming, but all the ways are not for all users.
DDoSing is one of many things a botnet can do. An other thing is malicious operations for example stealing files. A third thing is spamming (see Spam).
A single computer (maybe yours without you knowing it) in a botnet can automatically send thousands of spam messages per day. The most common spam messages come from zombie computers.
The herder may also rent the network to other cybercriminals. The botnet are very big business for criminals. We are talking about billion USD in one attack.
XtremBot, Agobot, Forbot, Phatbot: These are some of the best known bots with more than 500 versions in the internet today. The bot is written using C++ with cross platform capabilities as a compiler and GPL as the source code. These bots can range from the fairly simple to highly abstract module-based designs. Because of its modular approach, adding commands or scanners to increase its efficiency in taking advantage of vulnerabilities is fairly easy. It can use libpcap packet sniffing library, NTFS ADS and PCRE. Agobot is quite distinct in that it is the only bot that makes use of other control protocols besides IRC.
UrXBot, SDBot, UrBot and RBot: Like the previous type of bot, these bots are published under GPL, but unlike the above mentioned bots these bots are less abstract in design and written in rudimentary C compiler language. Although its implementation is less varied and its design less sohisticated, these type of bots are well known and widely used in the internet.
GT-Bots and mIRC based bots: These bots have many versions in the internet mainly because mIRC is one of the most used IRC client for windows. GT stands for global threat and is the common name for bots scripted using mIRC. GT-bots make use of the mIRC chat client to launch a set of binaries (mainly DLLs) and scripts; their scripts often have the file extensions .mrc.
Botnet spread
Botnets can also be used to spread other botnets in the network. It does this by convincing the user to download after which the program is executed through FTP, HTTP or email.
Browser hijacker
A type of malware that alters your computer's browser settings so that you are redirected to websites that you had no intention of visiting. Most browser hijackers alter browser home pages, search pages, search results, error message pages, or other browser content with unexpected or unwanted content.
Brute-force attack
A method of password cracking whereby all possible options are systematically enumerated until a match is found. These attacks try every passwords or encryption keys (or authentication option), one after another, until successful.
Brute-force often follows a Dictionary attack, if the Dictionary attack has failed. Many hackers custom made their dictionaries. Many hackers program their own brute-force algorithm.
An algoritm that can be quite simple.
Why Brute-force? Sometimes you need gain access to a target, or you need assess to the password strength on an existing web system. It has become more common for web systems to have brute-force protection. Brute-force protection can be a captcha, a simple math equation or a login token that has to be submitted with the request. There are a number of brute forcers that can do the brute-forcing of a post request to the login script, but in some cases they are not flexible enough to deal with dynamic content or handle “are you human” checks. But. This you can cure if you can program your own brute forcer.
With other words it's not true that brute-force are easy to discover. Not brute-forcers made by 1337.
In many cases where you’re attacking a custom web application or large system, you don't know about all files on the server. This you can cure if you can program your own spider, to crawl the target in order to discover the application. However in a lot of cases there are configuration files, leftover development files, debugging scripts, and other breadcrumbs that can provide sensitive information or expose functionality that the software developer did not intend. The only way to discover this content is to use a brute-forcer. Once again.
This you can cure if you can program your own brute forcer.
How complex and long the combination is a key factor, and if the password is found in a dictionary or not. A rule is that it's better to have a long password with letters that a short password with letters, numbers and symbols. Another rule is never use one username to all accounts. Remember also that many brute-forcers can translate @ to a and so on. Too many targets are lazy when "changing" their passwords from an account to an account.
How fast goes a brute-force attack? It depends.

A standard PC keyboard has today 104 keys incl. function keys.
A traditional PC keyboard had 84 keys.
An US keyboard has 101 keys.
An EU keyboard has 102 keys.
Brazilian, Chinese (the picture shows a keyboard from Taiwan), Korean, Japanese among other keyboards have even more keys.
What does this mean? It means in the end that a hacker should undergo language training.
As a curiosity I can mention that some languages stand out when it comes to Internet traffic and attacks. The most common languages are: english, russian, italian, arabic, and chinese.
A four (4) character long password has 95^4 possible combinations in nordic countries.
In reality a four (4) character password only has 78^4 or 58^4 possible combinations.
58^4 possible passwords means that you only use high and low letters in a nordic alphabet (incl. Å, Ä, Ö).
78^4 possible passwords means that you only use high and low letters in a nordic alphabet, numbers and 10 most common symbols.
In english speaking countries you often can compensate the nordic alphabet with the 14 most common symbols. If your software allows it you should use all possible characters incl. space. Often however you have in english speaking countries 62 possible digits on every part of the password.
Password structure often follow known patterns. Passwords are more easily cracked that their mathematical probabilities indicate. It is a difference between theory and reality. (See Mask attack).
A password such as "1234" or "asdf" will be cracked in one (1) nanosecond. Not in seconds as the mathematical probabilities indicate.
A password with 58^4 possible passwords, such as "aecH", will be cracked in 0,0000305 minutes (0,00183 seconds).
Note. Less can be more. A password with 78^4 possible passwords, such as "2gY¤" takes 0,000084 minutes (approx 0,01 seconds) to crack. In other words a 78^4 is not automatically safer than a 58^4 password.
Average 78^4 password cracking time is 0,05 minutes (or approx 3 seconds).
A password with 78^8 possible passwords takes with Brute-force >35 days to crack with a high end commercial computer anno 2015. Average time for a high end private cracking computer anno 2015 is how ever six (6) days. With an average commercial computer anno 2015 it takes two (2) years. With a low end computer anno 2015 or older it can take up to four (4) thousand years.
The number of characters make a difference when it comes to brute-force.
A few years back commercial high end overclocked CPU with high end GPU can crack much faster than you read in Computer science books.
Today (2016) you can buy a dual Intel Xeon E5 v3 processors with total 36 core or a less expensive 6th generation i-7, 64 bit, eight (8) core, 14 nm, K, unlocked, overclocked >6GHz range on liquid nitrogen (with air >4,6GHz), Turbo Boost, eight (8) DDR4 with flat 3000 MHZ RAM and 8 GB in each. Plus for example two (2) or more of latest generation GPU e.g. Titan X. And so on until your money runs out.
A some years back we have Supercomputers. In the middle between high end PC and Supercomputers you have for example Sparc M7 based computers. The Sparc M7 processor outperforms an x86 E5 v3 chip by up to 10.8x on analytics queries, but when it comes to brute-force couple of Titan X in an i-7 combo are in i r l de facto faster.
An alternative many choose is built their own plattform without common brands.
This for security reasons.
Certain types of encryption, by their mathematical properties, can not be defeated by a brute-force attack. For example an one-time pad cryptography, where every cleartext bit has a corresponding key from a truly random sequence of key bits. Attacking such a system relies not on pure cryptography. It relies upon operators mistakes.
Even one high letter in a seven (7) character long 58^7 low letter password makes it up to 128 times harder to crack. This is math theory. In reality it is a difference between approx 0,0333333 minutes (or approx 2 seconds) and 4 minutes.
The same time it takes to make noodles and drink a glas Volt (Jolt) Cola.
So. Finally. How fast goes a brute-force attack?
The answer is: there is no straight answer. All depend on you, your PC, your software, your connection and your target.
Caller ID spoofing
This is the practice of causing the telephone network to display a false number on the recipient's caller ID. A number of companies provide tools that facilitate caller ID spoofing. Voice over Internet Protocol (VoIP) has known flaws that allow for caller ID spoofing. These tools are typically used to populate the caller ID with a specific bank or credit union, or just with the words "Bank" or "Credit Union."
Carding
A technique used by thieves to verify the validity of stolen card data. The thief will use the card information on a website that has real-time transaction processing. If the transaction is processed successfully then the thief knows the card is still good. The purchase is usually for a small amount to avoid using the card's limit and to avoid attracting the attention of the card owner.
Clickjacking
Clickjacking is a term first introduced by Jeremiah Grossman and Robert Hansen in
2008. It describe a technique whereby an attacker tricks an user into performing certain actions on a website by hiding clickable elements inside an invisible iframe.
The attack allows to perform an action on victim website.
When an attacker uses multiple transparent or opaque layers to trick an user into clicking on a button or link on another page, when they were intending to click on the the top
level page. Thus, the attacker is "hijacking" clicks meant for their page and routing them to other another page, most likely owned by another application, domain, or both. It may be similar to CSRF (Cross Site Request Forgeries Attack).
Using a similar technique, keystrokes can also be hijacked. With a carefully crafted combination of stylesheets, iframes, and text boxes, a user can be led to believe they
are typing in the password to their email or bank account, but are instead typing into
an invisible frame controlled by the attacker.
At present this attack mostly use on social network websites like Facebook and twitter, Because this attack is used by convinced victim for click on the link and SocialNetwork website might be very useful for attack on victim.
Clone phising
The hacker change an existing email from e.g. your father and put a false link in it. The idea is trick you to provide personal information.
Code
Text based introductions. The spine in programs and devices. If a hacker change the code the program or device will act different, for example collect information of you and send it to the hacker
Complier
You could say a translator between different computer languages. A change in the compliner can create a back door. So when I for example now create my own OS, then I am tired in "oligopol Patch-OS' ", I program in assembly. I always program closest possible the machine code and use machine code if possible. I want feel the computer in my fingertips. And it is safer.
Computer based attack A social engineering attack using computer resources such as e-mail and IRC.
Cookie
Small amounts of data generated by a website and saved by your web browser. Websites use cookies to identify users who revisit their sites, and are most commonly used to store login information for a specific site. When a server receives a browser request that includes a cookie, the server can use the information stored in the cookie to customize the website for the user. Whenever a user checks the box "Remember me on this computer," the website will generate a login cookie once the user successfully logs in. Each time users revisit the site, they may only need to enter their password or may not need to login at all. Cookies can be used to gather more information about a user than would be possible without them. Information can be used in cyber attacks.
Cracking
A method with the intent of the computer system to access data, software, and /or processing power. In the mid 80's cracking was to break into commercial computer games.
In time crackers become the "bad guys", and hackers become the "good guys", who followed the Hacker Ethics (see Hacker).
Today cracking have a broader sense, and are in nowadays in some original sentence rarely used.
Crime ware
Malicious software such as viruses, Trojan horses, spyware, and other programs used to commit crimes on the Internet including identity theft and fraud.
Criminal identity theft
When a criminal fraudulently identifies himself to police as another individual at the point of arrest. In some cases criminals have previously obtained state-issued identity documents using credentials stolen from others, or have simply presented fake identification.
CSS
'XSS' also known as 'CSS' - Cross Site Scripting. It is a very common vulnerability
found in Web Applications, 'XSS' allows the attacker to insert malicous code, There are many types of XSS attacks. This kind of vulnerability allows an "attacker" to inject some code into the applications affected in order to bypass access to the website or to apply "phishing" on falls users. This technique is also used for website Hacking.
DOM-Based: The DOM-Based Cross-Site Scripting allow to an attacker to work not on a victim website but on a victim local machine: the various operative system usually includes "since born" some HTML pages created for differents aims, but as long as the humans do mistakes this HTML pages often can be exploited due to code vulnerabilities.
The DOM-Based XSS exploits these problems on users local machines in this way:
- The attacker creates a well builded malicious website
- The ingenuous user opens that site
- The user has a vulnerable page on his machine
- The attacker's website sends commands to the vulnerable HTML page
- The vulnerable local page execute that commands with the user's privileges
on that machine.
- The attacker easily gain control on the victim computer.
Non-Persistent: The non-persistent XSS are actually the most commons vulnerabilities that can be found on the Net. It's commonly named as "non-persistent" because it works on an immediate HTTP response from the victim website: it show up when the webpage get the data provided by the attacker's client to automatically generate a result page for the attackers himself. Standing on this the attacker could provide some malicious code and try to make the server execute it in order to obtain some result.
The most common applying of this kind of vulnerability is in Search engines in website: the attacker writes some arbitrary HTML code in the search textbox and, if the website
is vulnerable, the result page will return the result of these HTML entities.
Persistent: The persistent XSS vulnerabilities are similar to the second type (Non-persistent XSS), because both works on a victim site and tries to hack users informations and the difference is that in websites vulnerables to Persistent XSS the attacker doesn't need to
provide the crafted url to the users, because the website itself permits to users to insert fixed data into the system: this is the case for example of "guestbooks". Usually the users uses
that kind of tool to leave messages to the owned
of the website and at a first look it doesn't seems something dangerous, but if an
attacker discover that the system is vulnerable can insert some malicious code in his
message and let all visitors to be victim of that.
This works when the tool provided (the guestbook in the example) doesn't do any
check on the content of the inserted message: it just inserts the data provided from
the user into the result page.
Cyberbullying
Bullying that takes place in cyberspace. This includes the Internet and mobile phone communication. It may involve harassing, threatening, embarrassing, or humiliating someone online.Cyberbullying has become a huge problem in western democraties. It is used by all ages and backgrounds. It has nothing to do with freedom of speech.
In nordic countries as Sweden trade unions use cyberbullying as a weapon in industrial conflicts (see Doxing).
Good legal landmark: If it is a crime in the physical world, it is a crime online.
If you are a free spirit then at least remember - do not do toward others, what you do not want them do to you.
The last 25 years seem to show that also respected hackers can end up in bad standing and been cast out from the scene, not to mention the less respected hackers.
Cybercrime
A criminal activity done using computers and the Internet. This can take many shapes and forms, such as downloading illegal music files to stealing money from online bank accounts. Cybercrime can also include nonmonetary offenses, such as creating and distributing viruses. One of the most prominent cybercrime offenses is when cyber criminals use the Internet to steal personal information from others and commit identity theft.
Cyber criminals
Cyber criminals are black hat hackers, crackers, and other malicious users who use the Internet to commit crimes such as identity theft, PC hijacking, illegal spamming, phishing and pharming, and other types of fraud.
Cyber gangs
Cyber gangs are groups of hackers, crackers, and other cybercriminals that pool their resources to commit crimes on the Internet. Organized crime is often involved in cyber gang activity.
Cybersquatting
Registering, trafficking in, or using a domain name with malicious intent to profit from the goodwill of a trademark or brand name belonging to someone else. The cyber squatter then offers to sell the domain to the person or company who owns a trademark contained within the name at an inflated price. Cyber squatters also sometimes register variations of popular trademarked names as a way of distributing their malware.
Data
A broad term to describe information that has been translated into a form that is more convenient to move or process. Data can be physical and/or virtual.
Data can be in the form of text documents, images, audio files, software programs, and many more forms. Data can be processed on a computer or a mobile device, such as a mobile phone or tablet.
Denial of service (DoS)
Denial of Service Attacks.
An attack whereby the hacker injects code into an otherwise legitimate web page, which is then clicked by other users or is exploited via Java or some other script method. The embedded code within the link is submitted as part of the client’s web request and can execute on the user’s computer.
A botnet can be used as a distributed denial of service weapon. A botnet attacks a network or a computer system for the purpose of disrupting service through the loss of connectivity or consumption of the victim network’s bandwidth and overloading of the resources of the victim’s computer system. Botnet attacks are also used to damage or take down a competitor’s website.
Fast flux is a DNS technique used by botnets to hide phishing and malware delivery sites behind an ever-changing network of compromised hosts acting as proxies.
Any Internet service can be a target by botnets. This can be done through flooding the website with recursive HTTP or bulletin-board search queries. This mode of attack in which higher level protocols are utilized to increase the effects of an attack is also termed as spidering.This is one of the simplies network attacks.
An attack specifically designed to prevent a system from functioning properly as well as denying access to the system by authorized users.
There are two main forms of DoS attacks:
a) DoS that crash services;
b) DoS that flood services.
Following DoS techniques can be used: App layer, Fragmentation overlap, ICMP floods, IP fragmentation, Loopback floods, Low rate, Nukers, Reflective amplification, SYN flood, UDP floods.
Hackers can cause DoS attacks by destroying or modifying data or by overloading the system's servers until service to authorized users is delayed or prevented.
Dialers
A program that typically dials a premium rate number that has per minute charges over and above the typical call charge. These calls are with the intent of gaining access to pornographic material. Dialers include software programs that redirect Internet connections to a party other than the user's default ISP and are designed to run up additional connection charges for a content provider, vendor, or other third party.
Dictionary attack
Method of breaking into a password-protected computer, mobile device, or online account by entering every word in a dictionary as a password.
Directory traversal attack Also known as the dot-dot-slash attack. Using directory traversal, the attacker attempts to access restricted directories and execute commands outside intended web server directories by using the URL to redirect to an unintended folder location.
Distributed denial of service (DDoS)
A denial-of-service technique that uses numerous hosts to perform the attack.
With other woeds a type of denial-of-service (DoS) attack in which more than one traffic generator directs traffic to a targeted URL. Traffic-generating programs are called agents. Agents are hosts and the controlling program is the master. Agents are hosts to by the attacker installed daemons a k a demons. The distinction is that demons are usually processes within a program, while daemons are usually programs running on an operating system. Daemon was original introduced by CTSS people who pronounced it dee'mon, and used it to refer to what is now called a dragon a k a phantom. Daemon is a program which is not invoked explicitly, but which lays dormant waiting for some conditions to occur. The idea is that the perpetrator of the condition need not be aware that a daemon is lurking (See bot and bonet).
DoS agents receive instruction from a master to carry out an some of flooding DoS attack, which is designed to disable or shut down the targeted URL. Not only large numbers of hosts attacks once, creating a flood, DDoS also makes it more difficult to backtrack the attacker.
Also countries use DDoS toward other countries and sometimes toward their own citizens. E.g. 2011 UK's GCHQ JTRIG targeted Anon ops' communication infrastructure.
Downloader
Downloader is a trojan (see Trojan). Downloaders can download and install new versions of malicious programs onto your computer e g trojans and adware.
Doxing
The process of searching for and publishing private information about a target (usually an individual) on the Internet, typically with malicious intent.
A k a Internet-hate. Trashing victim with rumours on Internet toiletts such as e.g. Flashback.
Often the rumours are false, but they are spead as if the where true. Legally it does not matters if the rumours are true or false. It is unlegal anyway to slander people. The crime is done in that country the doxing are taking place. It do not matters where the server are. For example the Flashback Administrator1, let's call him "Axel", could be sentenced in Sweden despite the servers are in tax heaven under US juridiction.
There have been doxing cases when the victim has been doxed year after year.
There have been doxing cases that have ended in suicide.
Doxing is one of favorite choices of left-wing extremists such as trade union members and supporters, and right-wing extremists. These goons a k a trolls seem often to be low life wannabee hackers that thinks they are hackers just because they use VPN and belives they are safe from backtracking.
A pro seem to put his or her energy on creative things such as helping democratic movements such as the Arab Spring or counteract terrorists (see OpISIS), and tracking down undemocratic forces. Forces who want to pull the Internet plug and shut down the Free world.
One part of doxing can be False flag. False flag is a secret intervention. It can be made by private interests, but often by governments. The idea is by this perform a controversial action on behalf of a political group to seed mistrust and controversy. The idea with this is to provide justification for the government's own escalated response toward the target group.
The response can be harder legislation anno "1984" and/or hitting down with methods that in 80's would have been seen as pure "KGB"-methods.
Drive-by download
A program that is automatically downloaded to your computer without your consent or even your knowledge. It can install malware or potentially unwanted programs merely by your viewing an email or website.
If you have right software you can follow irl when your official Internet computer counter act drive-by downloads. Quite common.
Dropper
Dropper is a trojan. These programs are used by hackers in order to install trojans and / or viruses or to prevent the detection of malicious programs. Not all antivirus programs are capable of scanning all of the components inside this type of trojan. This is an executable file, created specifically to introduce a virus, worm, or trojan on a computer system.
Dumpster diving
The practice of sifting through commercial or residential trash in the hopes of finding information to steal or commit fraud.
Encryption
Encryption is a security method of coding or scrambling data so that it can be decoded or read only by authorized users. This is commonly used to secure websites, online purchases, and other transactions.
Executable file (.exe)
A type of computer file that when opened runs a program or series of instructions contained in the file. These types of files have the potential to be dangerous since they run code when opened, and are often used by cybercriminals to distribute viruses, malware, and spyware.
Exploit
Exploits take advantage of weaknesses or “vulnerabilities” in common software. It can be a bug, glitch, or design flaw in software in order to cause unintended or unanticipated behavior on computer software. Exploits you can find in e.g. Java and Adobe Flash.
A vulnerability is like a hole in your software that malware can use to get onto your PC. Malware can use these vulnerabilities to exploit the way the software works and further infect your PC (see Backdoor, Hole).
Some of the worst exploits allow attackers to run malicious code on your PC without your knowledge.This can include gaining control of a computer system, changing access privileges, or denying access or resources to users.
Often an exploit detection on your PC is just one piece of an larger attack. Malicious hackers can use a large number of exploits to infect your PC with as much malware as they can. Attackers might use an exploit kit to find vulnerabilities on your PC, which they can then try to exploit. An exploit kit is a hack toolkit that cybercriminals have favored in the last years to perform cyber attacks to distribute malware (see Malware).
Several kits have been developed and sold or rented out like commercial products in underground markets. The earliest exploit kit made available in the crimeware
market was in 2006.
You are exposed to the kit through e.g. visiting a compromised website. This often without knowing it. The compromised website contacts / redirect you to a website / server with an exploit kit. The website / server with the kit analyze your PC and localize what your PC are vulnerable to. After that the website with the kit contact your PC in different ways with different exploits. Depending what the cybercriminal want to do with you and your PC.
If your security software detects an exploit in e.g. your Javacache, it’s likely that an attempt to compromise your PC has been made. You have been pwn.
eZula
Ezula a k a eZula is a form of adware installed as part of a browser helper object. Without the user's permission, eZula communicates with a remote server and displays context-based advertisements to the individual.
Ezula contains no dangerous viruses, but can slow a user's browser and has to be manually installed by the user.
FakeAV
FakeAV is a trojan. FakeAV programs simulate the activity of antivirus software. They are designed to extort money from you – in return for the detection and removal of threats… even though the threats that they report are actually non-existent.
False negative
An error that occurs when antivirus software (AV) fails to detect that an infected file is truly infected. False negatives are more serious than false positives, although both are undesirable. False negatives are more common with antivirus software because they may miss a new or a heavily modified virus.
False positive
An error that occurs when antivirus software (AV) wrongly claims that a virus is infecting a clean file. False positives usually occur when the string chosen for a given virus signature is also present in another program.
Fuzzing
Fuzzing is a software testing technique, often automated or semi-automated, that
involves providing invalid, unexpected, or random data to the inputs of a computer program. The program is then monitored for exceptions such as crashes, or failing built-in code assertions or for finding potential memory leaks. Fuzzing technique is commonly used to test for security problems in software or computer systems ans also used to discover coding errors and security loopholes in software, operating systems
or networks by inputting massive amounts of random data, called fuzz, to the system
in an attempt to make it crash. If a vulnerability is found, a tool called a fuzz tester (or fuzzer), indicates potential causes.
There are two forms of fuzzing program; mutation-based and generation-based, which can be employed as white-, grey- or black-box testing. File formats and network protocols are the most common targets of testing, but any type of program input can
be fuzzed. Interesting inputs include environment variables, keyboard and mouse events, and sequences of API calls. Even items not normally considered "input" can be fuzzed, such as the contents of databases, shared memory, or the precise interleaving
of threads.
Forensics
Forensic science is the application of science to criminal and civil laws. Forensic scientists collect, preserve, and analyse scientific evidence during the course of an investigation. While some forensic scientists travel to the scene to collect the evidence themselves, others occupy a purely laboratory role, performing analysis on objects brought to them by other individuals. Digital forensics analysis is usually seen as a specialised domain of information and communication technologies (ICT) that is employed when a serious crime involving ICT is committed.
GameThief
GameThief is a trojan. This type of program steals user account information from online gamers.
Geolocation
Term used to describe the capability to detect and record where you and other people are located. Geolocation information can be obtained in a number of ways, including using data from a user's IP address, MAC address, RFID, Wi-Fi connection location, or GPS coordinates. Geolocation can also of hackers be used to locate and direct their malware in right direction. It also saves the hacker time when launching next attack.To locate the target hackers can use commercial everyday programs. This is the first step.
Geotagging
Process of adding geographical identification data to various types of media, such as a photograph or video taken with your camera or mobile device. This data usually consists of latitude and longitude coordinates, and they can also contain altitude, bearing, distance, and place names. A skilled hacker can change or erase geotagging.
If your surfing habbits are tracked you can be served with infected media. In the same way as e.g. browswers such as Google only serve you hits that match your past habbits.
Goon
Trolls' internal name of themself (see Troll).
Gray hat hackers
Skilled hackers who sometimes act legally, sometimes in good will and sometimes not. They are a hybrid between white and black hat hackers. They usually do not hack for personal gain or have malicious intentions, but may or may not occasionally commit crimes during the course of their technological exploits.
Hack
Originally a quick job that produces what is needed, but not well. In 50's, 60's, 70's a clever technique or practical joke. From 80's to work on a program and to pull a prank.

Hacker (Hacking)
Originally "hacking" means someone who makes furniture with an axe. After that the word got a wider meaning.
The first hacks in meaning exploits was performed with first telephones in 19th century.
Hacking started in the 20th century mean a person who perform his / her work in a passionate way, not only as a 9-5 work.
The red core is that you could be a "hacker" without knowing anything about computers.
Since 50's a hacker is basic a person who do not accept that something is in a specific way.
A hacker is a critical thinking person. He or she ask him- or herself- why is something in a specific way and what happens if I change the way? If they do not know right away how to change the way, they seek and learn themself, the tools needed to change the way. In the begining this critical thinking lead to lot of pranks.
The original hackers, the hacker generation 1, was a group tech students at MIT, USA, and the year was 1958. This was years before the pre-Internet in late 60's, 70's and 80's. The hacker generation 2 and 3 was active in this period. Among them my brother.
In 80's the hacker was a term used to describe a programmer who had a curiosity and appreciation of programs and systems and how they worked.
Over time, however, the term gained a negative connotation and began to refer to someone who uses the knowledge to break into other people's systems to steal information and cause harm.
In 80's we also called programmers who used their skills for harm, for "crackers."
In early days, back in 80’s, we called crackers those who cracked e.g. commercial computer games. I don't mention cracking movies, then movies in those days was on Betamax, Video-2000 and VHS. There was no need to crack movies. You just pressed REC.
Today hacking is a broad term for a person who uses programing skills and technical knowledge to create and modify computer software and hardware by finding weaknesses and exploiting them, including computer programming, administration, and security-related items. A hacker is a wizard. A hacker is a person who enjoys learning the details of programming systems and how to stretch their capabilities, as opposed to most users who prefer to learn only the minimum necessary a k a user a k a luzer. A hacker is someone who programs enthusiastically, or who enjoys programming rather than just theorizing about programming. A hacker is a person capable of appreciating hack value. A hacker is a person who is good at programming quickly. Not everything a hacker produces is a hack.
A hacker is an expert at a particular program, or one who frequently does work using it or on it.
A hacker can in nowadays also mean a malicious or inquisitive meddler, who tries to discover information by poking around. Hence "password hacker", "network hacker" etc.
Hackers can be motivated by a number of reasons both positive and negative, such as profit, protest, or challenge. Hackers, often criminal hackers a k a black hats, create malware in order to commit crimes, but malware can also as e.g. in my case be created by white - and grey hats, as an intellectual challenge.
"Older" hackers call technical educated persons with no real self-made hacking knowledge for skids a k a script kiddies. Older hackers with roots in 80's can sometimes call themself 1337, as in Leet, as in Elite.
Hijacker
A program that attempts to hijack certain Internet functions like redirecting your start page to the hijacker's own start page, redirecting search queries to a undesired search engine, or replace search results from popular search engines with their own information.
Hole
A vulnerability in the design software and/or hardware that allows the circumvention of security measures. All Windows owners are familiar with the patching-tuesday, the patch-day. A day once a week when holes in Windows are patched. There are also some ports' that often are used by hackers and can been seen as holes (see Exploit).
Host
A term often used to describe the computer file to which a virus attaches itself. Most viruses run when the computer or user tries to use the host file.
ICT
Information and communications technology (ICT) is often used as an extended synonym for information technology (IT), It is a more extensive term (i.e. more broad in scope) that stresses the role of unified communications and the integration of telecommunications (telephone lines and wireless signals), computers as well as necessary enterprise software, middleware, storage, and audio-visual systems, which enable users to access, store, transmit, and manipulate information.
In the wild (ITW)
A virus is "in the wild" (ITW) if it is verified as having caused an infection outside a laboratory situation. Most viruses are in the wild and differ only in prevalence.
Infected
This term refers to the condition of a file after a virus, spyware, or malware has inserted malicious code into it. Computer systems are infected if a virus or Trojan is installed and running on that system. Static malware, such as viruses and Trojans with entirely malicious code, is also said to be infected. If a potentially unwanted program is installed on a system, the system is not considered infected, even though there may be other consequences.
Infection
Infection is the action a virus carries out when it enters a computer system or storage device.
Information harvesters
People who supply stolen data but do not necessarily use it to commit fraud. The information obtained by harvesters is sold to criminal networks that trade the information in Internet back alleys.
International Mobile Equipment Identity (IMEI)
A number 15 or 17 digits in length that is unique to each mobile phone and tablet. It is used to identify users on the Global System for Mobile Communications (GSM) and the Universal Mobile Telecommunications System (UMTS). It is usually found printed inside the battery compartment of the phone. If a mobile phone is lost or stolen, the owner can call the network provider and instruct them to blacklist the phone based on the IMEI number and make it useless on the network.This is a good thing. The back side is with little critical thinking that it does not help change for example a cash SIM card inside a mobile, if the idea is to be incognito. Not even in non-smartphones. You must change the whole mobile incl. the cash card. Welcome to "1984".
International Mobile Subscriber Identity (IMSI)
A unique identification associated with all Global System for Mobile Communications (GSM) and Universal Mobile Telecommunications System (UMTS) network mobile phone users.
The IMSI is a unique number identifying a GSM subscriber stored inside the subscriber identity module (SIM).
Internet Protocol (IP) address
An IP address is a unique numerical label assigned to a device, such as a computer or other device on a network, including the Internet. IP addresses allow computers, routers, printers, and other devices to identify one another to communicate. Today we are running out of IP, but there are solutions.
IM
IM is a trojan. IM programs steal your logins and passwords for instant messaging programs, such as ICQ, MSN Messenger, AOL Instant Messenger, Yahoo Pager, Skype among others.
IT
Information technology (IT) is the application of computers and telecommunications equipment to store, retrieve, transmit and manipulate data.
Jailbreaking
Process of removing limitations imposed by Apple on devices running the iOS operating system (iPhone, iPad, and iPod). Users do this to gain root access to the operating system to be able to install apps obtained through means other than the official App Store. While this can allow the user greater control of what is installed on the device, it can also cause data corruption and make the device less secure.
Keylogger (keystroke logging)
An encryption software within the victims’ units can deter most bots from harvesting any real information. Unfortunately, some bots have adapted to this by installing a keylogger program in the infected machines. With a keylogger program, the bot owner can use a filtering program to gather only the key sequence typed before or after interesting keywords like PayPal or Yahoo mail. This is one of the reasons behind the massive PayPal accounts theft for the past several years.
Bots can also be used as agents for mass identity theft. It does this through phishing or pretending to be a legitimate company in order to convince the user to submit personal information and passwords. A link in these phishing mails can also lead to fake PayPal, eBay or other websites to trick the user into typing in the username and password.
Keylogger is a Software and/or hardware that tracks or logs the keys struck on a keyboard, typically in a covert manner, so that the person using the keyboard is unaware that their actions are being monitored. This is usually done with malicious intent to collect information including instant messages, email text, email addresses, passwords, credit card and account numbers, addresses, and other private data.
You can also plant a keylogger in the keyboard. A better way then few of us have as routine to check our hardware. And even if we did, few of us can see if there is a keylogger in our hardware.
The third way is to sniff. Modern keyboards are wireless, but modern keyboards use cryptated communication.
A fourth way, is something I learned in school in 90's, but it still works. Sniffing with laser. You need a specifik equipment and software, but when you have it, you can read keystrokes by reading the window glass.
How many offices (public or private) have you been in and seen proper saftey measures to avoid keyloggers? I thought so - zero.
Loader
A malware that sits silently on an infeced PC and awaits a trigger for example an additional binary payload before being executed.
Logic bomb
A virus that triggers a malicious action in the PC when certain conditions are met.
Mail bomb
An excessively large email (typically many thousands of messages) or one large message sent to a user's email account. This is done to crash the system and prevent genuine messages from being received.
Malware
A generic term used to describe any type of software or code specifically designed to exploit a computer or the data it contains, without consent. Malware includes viruses, Trojan horses, spyware, certain types of adware, most rootkits, and other malicious programs.
Malware is programming or files that are developed for the purpose of doing harm.
My personal favorit is polymorphic printable ASCII Shellcode. This means a shellcode that changes itself. It modifies the string it uses while it is running. The key is write shellcode that can pass the character check. At the same time it must be small. The solution is to write shellcode that built complex shellcode on the stack. The printable shellcode are in this way instructed to make the real shellcode.
Pure art.
With that said also countries use malware toward other countries and toward their own citizens. In Sweden PM Stefan Löfvens' government suggested 2015 putting malware in (all) Swedish citizens coumputers and 2016 to censorship the Internet in order to control the fractal chaos and diversity of Internet.
This is a difference between e.g. Stuxnet which targeted precise targets and e.g. "Stefan Löfven trojans" which will target every vessel and in the end the whole high sea.
Malicious code
A piece of code designed to damage a system and the data it contains, gather sensitive information, gain unauthorized access, or to prevent the system from being used in its normal manner.
Malicious app
A mobile application (app) disguised as a legitimate app that can contain viruses, worms, Trojan horses, malware, spyware, or any other items that may harm user devices or personal data. Once a malicious app is downloaded, it can wreak havoc in multiple ways including sending text messages to premium-rate numbers, taking control of the infected device, and downloading the user's contact lists. Cybercriminals distribute malicious apps through legitimate app stores like Google Play by masquerading as a legitimate app.
Man-in-the-Middle (MitM) Attacks
This is one way to combat encryption. The attacker sits between the target and the target hosts. Both target and the host believes they are communicating with each other, but they are communicating with the attacker. This means when target is opening an encrypted communication with the host through an asymmetric communication, the attacker gets the secret key. After this the attacker open a communication with the host and gets the secret key from the host. The attacker decrypt the packets with the first key and re-encrypts them with the second key. The hacker use two main tools, one ARP-tool to redirect the traffic and one SSH-MitM tool. You can also MitM in other situations.
Mask attack
A traditional Brute force attack (see Brute force attack) require a charset that contains all upper-case letters, all lower-case letters and all digits. As we saw above there are
at least 58 combinations of every digit.
A mask attack is a word generator with a per-position configureable charset. It will try all combinations from a given keyspace just like in Brute force attack, but it is more specific.
If the Password is e.g. "Petra2002", then the password length is 9 digit. This mean we have to iterate through 62^9 (13.537.086.546.263.552) combinations, if we are in a english speaking country. 58^6 or 78^6 if we are in a nordic country.
Let's say we crack with a rate of 100M/s, a 62^9 requires more than four (4) years with an avarage PC anno 2015 and Brute force to complete. A mask attack is always specific to a password length. Thats why you have to repeat the attack several times, each time with one placeholder added to the mask.
The idea with mask attack is that we know about humans, how they design passwords. Propably we know about our target through data mining. The above mentioned password matches a common pattern. Humans love their or their love one names and year of birth. We can also configure the attack to try the upper-case letters only on the first position.
It is very uncommon to see an upper-case letter only in the second or the third position. With mask attack you can reduce the keyspace on a 62^9 to 522626262610101010 combinations. With the same cracking rate of 100M/s, this requires just 40 minutes to complete. Voila.
Network
A network can consist of two or more computers, mobile devices (phones and tablets), gaming devices, Internet connected TVs, etc. connected to each other.
Networks can be connected by cables or wirelessly. The purpose of a network is to share files and information.
Password attack
An attempt to obtain or decrypt a user's password for illegal use. Hackers can use cracking programs, dictionary attacks, and password sniffers in password attacks. Defense against password attacks is rather limited, but usually consists of a password policy including a minimum length, unrecognizable words, and frequent changes (see Brute-Force attack for pro bono tip).
Password cracker
Software designed to enable a user or administrator to recover lost or forgotten passwords from accounts or data files. In the hands of an attacker, these tools offer access to confidential information and are a security and privacy threat.
Remember: If the attacker has the hardway in his or her hand, then there are also other ways. And I am not talking about pressing ESC. So, don't forget physical protection e.g. locks on doors, safe the windows, have a alarm with dial-up, cameras with HD recording, lock HD in a safe, bolt the safe, lock your computer in your desk, encryption etc.
Common sence.
Password sniffing
The use of a sniffer (software or a device that monitors a network and makes a copy of data sent over a network) to capture passwords as they cross a network. The network could be a local area network, or the Internet itself.
This have been a problem since at least 15 years. First the sniffers was used against businessmen for example on airports. The attacker could sit in a car on a parkingspot outside the airport. The attacker sniffed the passwords and after that took the business secrets from the businessman. Too many was and are spending their time on Internet while waiting on their plane.Today also hackers use this method, but outside airports.
Password stealer (PWS)
Malware specifically used to transmit personal information, such as usernames and passwords.
Payload
The "cargo" code in a virus rather than the portions used to avoid detection or replicate. The payload code can display text or graphics on the screen, or it may corrupt or erase data. Not all viruses contain a deliberate payload. However, these codes affect CPU usage, hard disk space, and the time it takes to clean viruses. Payload can also refer to the data or packets sent during an attack.
Pay-Per-Click Systems Abuse
Botnets can be used for financial gain by automating clicks on a pay-per-click system. Compromised units can be used to click automatically on a site upon activation of a browser. For this reason, botnets are also used to earn money from Google’s Adsense and other affiliate programs by using zombies to artificially increase the click counter of an advertisement.
Peer-to-peer (P2P) networking
A distributed system of file sharing in which any computer on the network can see any other computer on the network. Users can access each other’s hard drives to download files. This type of file sharing is valuable, but it brings up copyright issues for music, movies, and other shared-media files. Users are also vulnerable to viruses, Trojans, and spyware hiding in files.
Personally identifiable information (PII)
Any information that, by itself or when combined with other information, can identify an individual.
Pharming
The process of redirecting traffic to a fake website, often through the use of malware or spyware. A hacker sets up a fraudulent website that looks like a legitimate website in order to capture confidential information from users.
Phishing
A form of criminal activity using social engineering techniques through email or instant messaging. Phishers attempt to fraudulently acquire other people's personal information, such as passwords and credit card details, by masquerading as a trustworthy person or business in an apparently official electronic communication. Typically, phishing emails request that recipients click on the link in the email to verify or update contact details or credit card information. Like spam, phishing emails are sent to a large number of email addresses, with the expectation that someone will act on the information in the email and disclose their personal information. Phishing can also happen via text messaging or phone.
Piggyback
The practice of gaining unauthorized access to a system by exploiting an authorized user's legitimate connection without their explicit permission or knowledge.
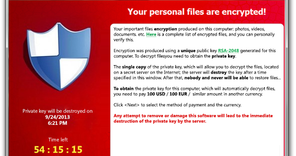
Ransomware
Malicious software created to restrict your access to your computer system. The idea is to infect your compuyter and demand a ransom paid to the creator of the malicious software for the restriction to be removed. Until you pay, the creator holds your PC or files for ransom.
Some forms of ransomware may also encrypt files on the system's hard drive, while others may simply lock the system and display messages to coax the user into paying.
There are different types of ransomware. However, all of them will prevent you from using your PC normally, and they will all ask you to do something before you can use your PC.
They can:
- Prevent you from accessing Windows.
- Encrypt files so you can't use them.
- Stop certain apps from running.
- They will demand that you do something to get access to your PC or files.
I have seen them:
- Demand you pay money.
- Make you complete surveys.
Often the ransomware will claim you have done something illegal with your PC, and that you are being fined by a police force or government agency e.g. FBI. These claims are false. It is a scare tactic designed to make you pay the money without telling anyone who might be able to restore your PC.
There is no guarantee that paying the fine or doing what the ransomware tells you will give access to your PC or files again.
To day the only cure to ransomware using RSA is to prevend.
Red Cell
Red Cell is originally an US military term. Red Cell is an organized mission to physical and / or virtual infiltrate and test an organization security.
Red Cell is not the same as a Red Team. The term Red Team is used when it comes to malware and reversed engineering, and in the US military and private companies, when it comes to forecast the future.
You could call my work as Historian in 90's, 00's, 10's for Red Cell operations.
The goal itself was not test an organizations security. The goal in those days was Data Mining for the best of science, and by extension for the best of Western democracy.
Redirect
A method used to direct someone or something to a different place than was intended. Cybercriminals can use these to route a legitimate website's traffic to a counterfeit website.
Remote administration tool (RAT)
Software a k a a trojan designed to give an oerator remote control of a system. Hackers can install malicious RAT software on a computer without the user's knowledge and take control of it remotely without the user's knowledge. RATs can be installed by hacking a system, byopening an infected attachment, an infected USB, by clicking links in a popup window, or through any other software that poses as legitimate.
To do this a black hat can e.g. have two files. One shell as the attachment and a RAT. He puts the RAT inside the attachment. After having married the RAT with the attachment he can put as option auto load and rename the whole attachment as e.g. something that sems to be legitmate as e.g. an important update from a known AV or OS company. After that he propably erase the two original files. Then a RAT is written in e.g. C/C++ the targets AV will not pay attention when the target downloads the "update". The RAT is thanks to C/C++ too small and are hiding inside a "legimate" attachment. After auto load the RAT is inside the system and put itself inside root as e.g. exe files. After this the black hat can remote controll the system, copy the system, infect the system with new files (docx, pdf, exe etc), shut down the system, erase the system, turn the GPS on, browse through the system, spy on the target through the mic and cam, listen to the target, record videos of the target and much more.
Replication
The process by which a virus makes copies of itself to carry out subsequent infections. Replication is one of the major criteria separating viruses from other computer programs.
Rogue program
Any program intended to damage programs or data, or to breach a system's security. It includes trojan horse programs, logic bombs, and viruses.
Rogue security software is a type of program that pretends to detect and remove malware for a fee. Rogues claim to scan for malware and then regularly show you fake detections and warnings. They tell you that you need to pay to register the software or remove the fake threats from your PC. Rogues try to scare you into paying a fee, in the hope that the rogue will clean your PC. They need to convince you to pay a fee to be successful. They usually target you with a lot of deceptive messages coming from their fake software, websites and messages.
Rogues are installed in similar ways to other malware. They can be:
- Downloaded and installed by other malware.
- Installed by exploiting vulnerabilities in particular software.
- Installed by social engineering.
Rooting
A way that users of mobile devices (mobile phones, tablet PCs, and other devices running the Android operating system) hack their devices to gain privileged access to the operating system. This gives the user the ability to alter or replace system applications and settings, run apps that require administrator permissions, or perform operations that otherwise would have not been possible.
Rootkits
A stealthy type of malware that is designed to hide the existence of certain processes or programs from normal methods of detection and enable continued privileged access to a computer. Malware authors use rootkits to hide malware on your PC. Malware hidden by rootkits often monitor, filter, and steal your data or abuse your computer’s resources. It means that after a rootkit is installed, you can’t trust any information that your PC reports about itself. For example, if you were to ask your PC to list all of the programs that are running, the rootkit might stealthily remove any programs it doesn’t want you to know about. In other words, rootkits are all about hiding things. They want to hide themselves on your PC, and they want to hide malicious activity on your PC.
Rootkits are the hardest type of invasive software to detect and nearly impossible to remove. As eluded to in the name, they dig into the root of a hard drive. They are designed to steal passwords and identifying information.
By using a rootkit, a hacker hopes to protect and maintain their hidden presence on your PC for as long as possible. A successful rootkit can potentially remain in place for years if it is undetected. All this time it will steal information and resources from your PC.
Scaning
One of the first methods I learned in school of all places back in 90's was scaning. When you write on your computer the text from your monitor can be scaned with laser from your window. An easy way to read what you are writing on your computer screen.
Scareware
A common trick cybercriminals use to make users think that their computer has become infected with malware to get them to purchase a fake application. Often the fake application that the user is tricked into purchasing is actually a malicious program which can disable real antivirus software and wreak havoc on a user's machine.
Shrink wrap code attack Attacks that take advantage of the built-in code and scripts most off-the-shelf applications come with.
Shoulder surfing
The use of direct observation techniques, such as looking over someone's shoulder, to get information. A criminal can get access to your personal identification number (PIN) or password by watching over your shoulder as you use an automated teller machine (ATM) or type on your computer.
Signature files
Data files containing detection and/or remediation code that antivirus or antispyware products use to identify malicious code.
SIM (subscriber identity module) card
A small electronic card, approximately the size of a postage stamp that is placed underneath a mobile phone's battery. The SIM card stores data such as user identity, location phone number, network authorization data, personal security keys, contact lists, and stored text messages.
SMiShing
The act of using social engineering techniques similar to phishing but via text messaging. The name is derived from "SMS (Short Message Service) phishing." SMS is the technology used for text messages on mobile phones. SMiShing uses text messages to try and get you to divulge your personal information. The text message may link to a website or a phone number that connects to automated voice response system.
Sniffer
Software or device that monitors network traffic. Hackers use sniffers to capture data transmitted over a network.
The sniffer can be both hard- and software. The poor man use mainly software. Mainly organized crime and gouverment can also use hardware. The hardware is installed in the main line to the target and read all traffic to and from the target. Algorithms sort the information out.
Social engineering
The act of manipulating people into performing actions or divulging confidential information. It relies on human interactions, such as trying to gain the confidence of someone through trickery or deception for the purpose of information gathering, fraud, or computer system access. This can take many forms, both online and offline.
Spam
A botnet can also be used to take advantage of an infected computer’s TCP/IP’s SOCKS proxy protocol for networking appications. After compromising a computer, the botnet commander can use the infected unit (a zombie) in conjunction with other zombies in his botnet (robot network) to harvest email addresses or to send massive amounts of spam or phishing mails.
Moreover, a bot can also function as a packet sniffer to find and intercept sensitive data passing through an infected machine. Typical data that these bots look out for are usernames and passwords which the botnet commander can use for his personal gain. Data about a competitor botnet installed in the same unit is also mined so the botnet commander can hijack this other botnet.
Access number replacements are where the botnet operator replaces the access numbers of a group of dial-up bots to that of a victim's phone number. Given enough bots partake in this attack, the victim is consistently bombarded with phone calls attempting to connect to the internet. Having very little to defend against this attack, most are forced into changing their phone numbers (land line, cell phone, etc.).
Spam is an unwanted electronic message, most commonly unsolicited bulk email. Typically, spam is sent to multiple recipients who did not ask to receive it. Types include email spam, instant messaging spam, web search-engine spam, spam in blogs, and mobile phone-messaging spam. Spam includes legitimate advertisements, misleading advertisements, and phishing messages designed to trick recipients into giving up personal and financial information. Email messages are not considered spam if a user has signed up to receive them.
Spear phishing
The act of sending an email that appears to come from a legitimate source, such as a bank, a company's internal IT department, an internal employee, or a business partner. While phishing uses mass email, spear phishing targets a very small number of recipients. The email sender information may be spoofed so the email appears to originate from a trusted source. Messages typically request username and password details, provide a link to a website where visitors can enter personal information, or have an attachment containing a virus, Trojan, or spyware.
Spim
A type of spam specific to instant messaging. The messages can be simple unsolicited ads or fraudulent phishing mail.
Splog
A combination of the words spam and blog that has been created for the purpose of distributing spam. Splogs contain fake articles created for search engine spamming. Splogs are created to attract people to spam sites, primarily via search engines.
Spoofed website
A website that mimics a real company's site—mainly financial services sites—in order to steal private information (passwords, account numbers) from people tricked into visiting it. Phishing emails contain links to the counterfeit site, which looks exactly like the real company's site, down to the logo, graphics, and detailed information.
Spoofing
Spoof means to hoax, trick, or deceive. Spoofing can take many forms on the Internet, like faking the email address of another user. You use e.g. spoofing in ARP-poisoning.
A spoofed website is e.g. one that mimics a real company's site—mainly financial services sites—to steal private information (passwords, account numbers) from people tricked into visiting it.
Spyware
Its a software which sends information to its creators about a user's activities – typically passwords, credit card numbers and other information that can be sold on the black market. Spyware can capture information like web browsing habits, email messages, usernames and passwords, and credit card informationCompromised machines that are located within a corporate network can be worth more to the bot herder, as they can often gain access to confidential information held within that company. There have been several targeted attacks on large corporations with the aim of stealing sensitive information, one such example is the Aurora botnet.
Just like viruses, spyware can be installed on a computer through an email attachment containing malicious software. What is the difference between e.g. spyware and malware? Spyware is malware. The word "spyware" describes what the code do. The word "malware" describes what the code is.
SYN flood attack A type of attack used to deny service to legitimate users of a network resource by intentionally overloading the network with illegitimate TCP connection requests. SYN packets are sent repeatedly to the target, but the corresponding SYN/ ACK responses are ignored.
TCP/IP Hijacking
This technique is used when the target use one-time password. The attacker sniff the network the target is on. While sniffing the attacker will got sequence of numbers for connection between the target and the targets host. Each TCP packet contains a sequence of numbers in its header. After this the attacker can send a spoofed packet with correct numbers to the host. The host believes that the packet comes from the targets computer.
Tiger Team
Tiger Team is originally an US military term. Tiger Team is a mission for the assembled group of experts, whose task is to investigate and / or resolve an organization technical and / or system problems.
Time bomb
A malicious action triggered at a specific date or time.
Tini A Trojan listening on port 777.
Trojan (Trojan horse)
A non-self-replicating program that appears to have a useful purpose but in reality has a different, malicious purpose.
A program that has been designed to appear innocent, but has been intentionally designed to cause some malicious activity or to provide a backdoor to your system.
This malicious program can e.g. disguise as legitimate software. They are called trojans because they are like the mythological wooden Trojan Horse that was used to sneak into the ancient city of Troy. Trojans are the most common type of malware. One key factor that distinguishes a Trojan from viruses and worms is that Trojans don't replicate. Unlike viruses, trojans can’t spread on their own – they rely on you to run them on your PC by mistake, or visit a hacked or malicious webpage. Users are typically tricked into loading and executing it on their systems.
A trojan might use the same file name as a real or legitimate app, so you might accidentally download a trojan, thinking you are downloading something else.
They are often installed with other types of malware, so it's unlikely you'll only get infected with one trojan and nothing else.
Trojans can come in many different varieties, but generally they do the following on your PC:
- Download and install other malware, such as viruses or worms (see Blended).
- Use your PC for click fraud.
- Record your keystrokes and the sites you visit.
- Send information about your PC to a malicious hacker, including your passwords,
login details for websites, and browsing history.
- Give a malicious hacker control over your PC.
Troll (see Goon)
A person who sows discord on the Internet by starting arguments or upsetting people, by posting inflammatory, extraneous, or off-topic messages in an online community, such as a newsgroup, forum, chat room, or blog, with the deliberate intent of provoking readers into an emotional response or of otherwise disrupting normal on-topic discussion, often for their own amusement. Lulzy messages. Not so lulzy to the victim.
Tunneling
A self-replicating malicious program that attempts installation beneath antivirus software by directly intercepting the interrupt handlers of the operating system to evade detection.
This is a virus technique designed to prevent antivirus applications from working correctly. Antivirus programs work by intercepting the operating system before it can execute a virus. Tunneling viruses try to intercept the actions before the antivirus software can detect the malicious code. New antivirus programs can recognize many viruses with tunneling behavior.
Typo squatting
Also known as URL hijacking, it relies on mistakes such as typographical errors made by Internet users when inputting a website address into a browser. If the user accidentally enters the incorrect website address, they are lead to an alternative website that usually is designed for malicious purposes.
Virus
A program that when run, has the ability to self-replicate by infecting other programs and files on your computer. These programs can have many effects ranging from wiping your hard drive, displaying a joke in a small box, or doing nothing at all except to replicate itself. These types of infections tend to be localized to your computer and not have the ability to spread to another computer on their own. The word virus has incorrectly become a general term that encompasses trojans, worms, and viruses.
Viruses are often by the AV industry divided by how they infect your computer: boot, file, macro and script. To a Creator it dosen't matter what a virus is called.
Boot Sector Virus. Boot sector viruses infect either the master boot record of the hard disk or the floppy drive. The boot record program responsible for the booting of operating system is replaced by the virus. The virus either copies the master boot program to another part of the hard disk or overwrites it. They infect a computer when it boots up or when it accesses the infected floppy disk in the floppy drive. While boot sector viruses infect at a BIOS level, they use DOS commands to spread to other floppy disks. For this reason, they started to fade from the scene after the appearance of Windows 95 (which made little use of DOS instructions). Today, there are programs known as ‘bootkits’ that write their code to the master boot record as a means of loading early in the boot process and then concealing the actions of malware running under Windows. i.e. Once a system is infected with a boot-sector virus, any non-write-protected disk accessed by this system will become infected. Examples of boot- sector viruses are e g Michelangelo and Stoned. The only absolute criteria for a boot sector is that it must contain 0x55 and 0xAA as its last two bytes. If this signature is not present or is corrupted, the computer may display an error message and refuse to boot. Problems with the sector may be due to physical drive corruption or the presence of a boot sector virus.
File or Program Viruses. Some files/programs, when executed, load the virus in the memory and perform predefined functions to infect the system. They infect program files with extensions like .EXE, .COM, .BIN, .DRV and .SYS .
Common file viruses are e g Sunday, Cascade.
Multipartite Viruses. A multipartite virus is a computer virus that infects multiple different target platforms, and remains recursively infective in each target. It attempts to attack both the boot sector and the executable, or programs, files at the same time. When the virus attaches to the boot sector, it will in turn affect the system’s files, and when the virus attaches to the files, it will in turn infect the boot sector.
This type of virus can re-infect a system over and over again if all parts of the virus are not eradicated. Ghostball was the first multipartite virus, discovered by Fridrik Skulason in October 1989. Other examples are e g Invader, Flip among others.
Macro Viruses. A macro virus is a computer virus that "infects" a Microsoft Word or similar application and causes a sequence of actions to be performed automatically when the application is started or something else triggers it. Macro viruses tend to be surprising but relatively harmless.A macro virus is often spread as an e-mail virus. Well-known examples are e g Concept Virus and Melissa Worm.
Metamorphic Viruses. A metamorphic virus is one that can transform based on the ability to translate, edit and rewrite its own code. It is considered the most infectious computer virus, and it can do serious damage to a system if it isn't detected quickly. Antivirus scanners have a difficult time detecting this type of virus because it can change its internal structure, rewriting and reprogramming itself each time it infects a computing system. This is different from a polymorphic virus, which encrypts its original code to keep from being detected. Because of their complexity, creating metamorphic viruses requires extensive programming knowledge.
Polymorphic Viruses. Polymorphic viruses have the ability to mutate implying that they change the viral code known as the signature each time they spread or infect. Thus an antivirus program which is scanning for specific virus codes unable to detect it's presense.
Stealth Viruses. These viruses are stealthy in nature means it uses various methods for hiding themselves to avoid detection. They sometimes remove themselves from the memory temporarily to avoid detection by antivirus. They are somewhat difficult to detect. When an antivirus program tries to detect the virus, the stealth virus feeds the antivirus program a clean image of the file or boot sector.
Vishing
The criminal practice of posing as a legitimate source to obtain information over the telephone system (phishing via phone/ voicemail). It is facilitated by Voice over IP because it can spoof (fake) caller ID to gain access to personal and financial information.
War dialing
Process in which a computer is used to automatically call a list of telephone numbers, usually dialing every number in a local area code to search for computers and fax machines that can successfully make a connection with the computer. When each call is made, the program makes a list of which numbers made a successful connection with a computer and a fax machine. That list can be later used by hackers for various reasons, including hacking a wireless access point with an unprotected login or an easily cracked password to gain access to a network.
War driving
The act of stealing personal information by driving around looking for unsecured wireless connections (networks) using a portable computer or a personal digital assistant (PDA).
If your home wireless connection is not secured, thieves can access data on all the computers you have connected to your wireless router, as well as see information you type into your banking and credit card sites.
Warez
A k a BoW. Pirate software.
Whaling
A type of scam in which phishers find the name and email address of a company's top executive or team of executives (information often freely available on the web), and craft an email specific to those people and their role at the company. The email attempts to lure the executives into clicking on a link that will take them to a website where malware is downloaded onto their machines to copy keystrokes or ferret out sensitive information or corporate secrets.
White hat hackers
Also known as "ethical hackers" a k a EH. White hat hackers are computer security experts who specialize in penetration testing and other testing methodologies to ensure that a company's information systems are secure. These security experts may utilize a variety of methods to carry out their tests, including social engineering tactics, use of hacking tools, and attempts to evade security to gain entry into secured areas.
Worm
A program that when run, has the ability to spread to other computers on its own using either mass-mailing techniques to email addresses found on your computer or by using the Internet to infect a remote computer using known security holes. Worm is a malware that spreads by creating duplicates of itself on other drives, systems, or networks. A mass-mailing worm is one that requires a user's intervention to spread, (e.g., opening an attachment or executing a downloaded file). Unlike viruses, worms do not infect other files. Most of today's email viruses are worms. A self-propagating worm does not require user intervention to spread.
Worms are often by the AV industry divided by how they infect your computer: Email, IM, IRC, Net and P2P. To a Creator it dosen't matter what a worm is called or how its subclassed by the AV industry.
Zero-day threats, zero-day vulnerabilities
Also known as zero-hour threats and vulnerabilities, they include threats that take advantage of a security hole before the vulnerability is known. The security hole is usually discovered the same day the computer attack is released. In other words, software developers have zero days to prepare for the security breach and must work as quickly as possible to fix the problem.
Zombie
A computer that has been compromised by a virus or Trojan horse that puts it under the remote control of an online hijacker. The hijacker uses it to generate spam or makes the computer unusable to the owner, and the user is usually unaware that their computer has been compromised. Generally, a compromised machine is only one of many in a botnet, and will be used to perform malicious tasks under remote direction.
Zoo virus
A virus found only in virus laboratories that has not moved into general circulation.
And last but not least. Zoo means virus collection for example in a Sandbox.
Petrus Toxy
/ Petrus Toxy
Founder of T Office - Offensive Network Security
Client Supra Omnes
Hire a lawyer and EH all-in-one, who thinks "outside the box".
Hire Petrus Toxy. I will point out the security weaknesses in your organization:
disloyal employees, whistle blowers and cyber criminals.
/ Petrus Toxy